Not long ago a group of researchers at computer security reported a RCE (Remote Control Ejecution) vulnerability in a subdomain of Yahoo.com. Good in this occasion I come to present this small tool group use to detect this vulnerability. Well no more to add, comensemos.
WebPwn3r is a scanner of vulnerabilities in web applications. This mentioned tool is written in the Python language, and as I mentioned above help researchers to scan multiple links at the same time, in search of CERs or some typical vulnerabilities XSS vulnerability.
WebPwn3r detections. (The public tool only has the options *)
Scan a URL or a particular list of URL's.
* Detect and exploit remote code injection vulnerabilities.
To detect remote command execution vulnerabilities.
* Detect typical vulnerabilities Cross Site Scripting (XSS)
Detect WebKnight WAF.
It improves the payload for bypass filters seguridad(WAF 's).
Notes and print backend technologies.
Notes:
1.-This tool can also extract the URL´s of Burp Suite then guardardo in a targets.txt, to finally file that the URL's are finally analyzed by WebPwn3r.
2. This tool has great potential, since the user could optimize it to create a powerful and effective Crowler who would search all subdomains of a given domain or domains, to then classify them and print them in .txt files, to then be analyzed with a variacon of WebPwn3r.
Well then I do a little test about WebPwn3r skills, for this I will use Windows 7, since I've previously installed packages of python 3.3.
Our goal for the test will be a subdomain of the Nato.
Aim: https://transnet.act.nato.int/
We entered option 1 since we are going to do tests on a single URL. Option 2 is for multiple objective analysis and rather than enter a URL, we will enter the name of the file that stores all the URLs that will be analyzed.
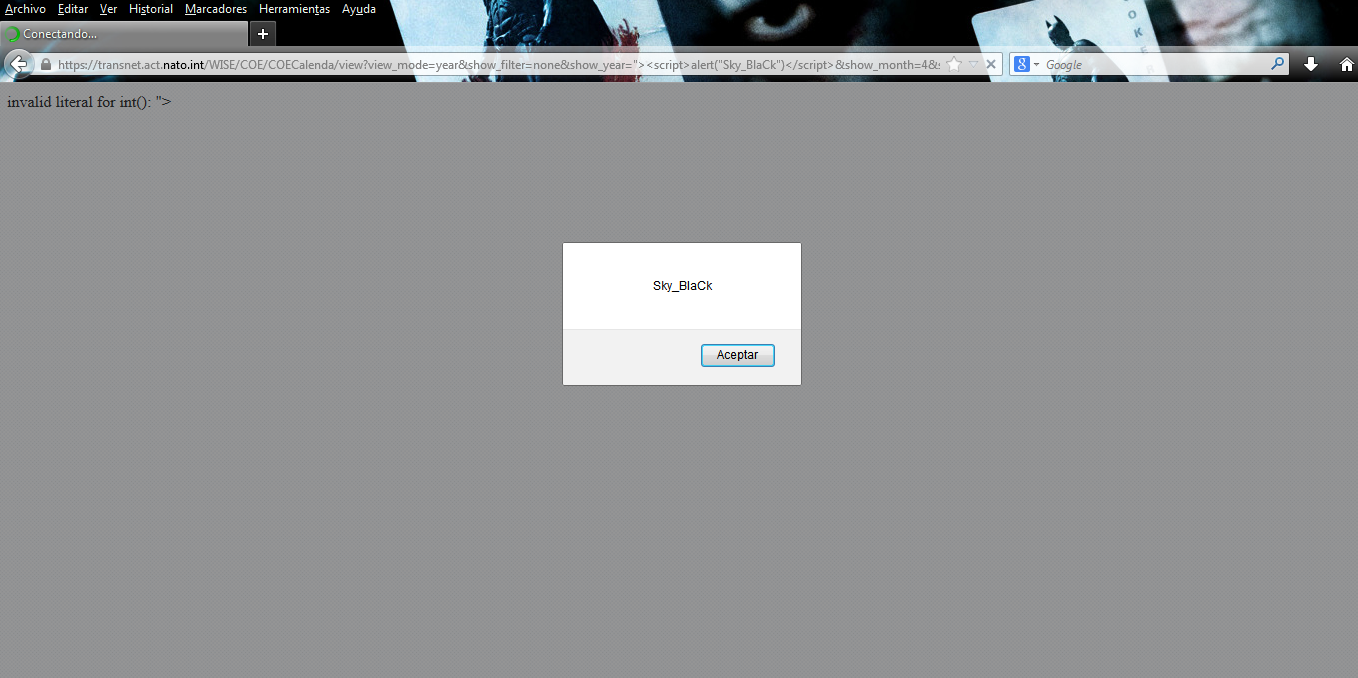
So far, we can see that our goal has no RCE vulnerability, but apparently if you have multiple Cross Site Scripting vulnerabilities.
Well according to this tool our goal has 94 Cross Site Scripting vulnerabilities. Interesting but apparently this in error. This large number is because the variables were subjected to different types of scripts, some ordinary and others duly obfuscated attacks.
Note: This vulnerability was one of the many vulnerabilities that I could find in the Nato, all vulnerabilities found them with my tool Minerva v.1.4, I have used this objective to simplify the post.
Well I think that we have reached the end of the post, I hope that this small tool will be useful and serve them in the future. See you and it will be up to the next.
Not long ago a group of researchers at computer security reported a RCE (Remote Control Ejecution) vulnerability in a subdomain of Yahoo.com. Good in this occasion I come to present this small tool group use to detect this vulnerability. Well no more to add, comensemos.
WebPwn3r is a scanner of vulnerabilities in web applications. This mentioned tool is written in the Python language, and as I mentioned above help researchers to scan multiple links at the same time, in search of CERs or some typical vulnerabilities XSS vulnerability.
WebPwn3r detections. (The public tool only has the options *)
Scan a URL or a particular list of URL's.
* Detect and exploit remote code injection vulnerabilities.
To detect remote command execution vulnerabilities.
* Detect typical vulnerabilities Cross Site Scripting (XSS)
Detect WebKnight WAF.
It improves the payload for bypass filters seguridad(WAF 's).
Notes and print backend technologies.
Notes:
1.-This tool can also extract the URL´s of Burp Suite then guardardo in a targets.txt, to finally file that the URL's are finally analyzed by WebPwn3r.
2. This tool has great potential, since the user could optimize it to create a powerful and effective Crowler who would search all subdomains of a given domain or domains, to then classify them and print them in .txt files, to then be analyzed with a variacon of WebPwn3r.
Well then I do a little test about WebPwn3r skills, for this I will use Windows 7, since I've previously installed packages of python 3.3.
Our goal for the test will be a subdomain of the Nato.
Aim: https://transnet.act.nato.int/
We entered option 1 since we are going to do tests on a single URL. Option 2 is for multiple objective analysis and rather than enter a URL, we will enter the name of the file that stores all the URLs that will be analyzed.
So far, we can see that our goal has no RCE vulnerability, but apparently if you have multiple Cross Site Scripting vulnerabilities.
Well according to this tool our goal has 94 Cross Site Scripting vulnerabilities. Interesting but apparently this in error. This large number is because the variables were subjected to different types of scripts, some ordinary and others duly obfuscated attacks.
Note: This vulnerability was one of the many vulnerabilities that I could find in the Nato, all vulnerabilities found them with my tool Minerva v.1.4, I have used this objective to simplify the post.
Well I think that we have reached the end of the post, I hope that this small tool will be useful and serve them in the future. See you and it will be up to the next.




.png)

.png)


.jpg)






