1) Phishing :
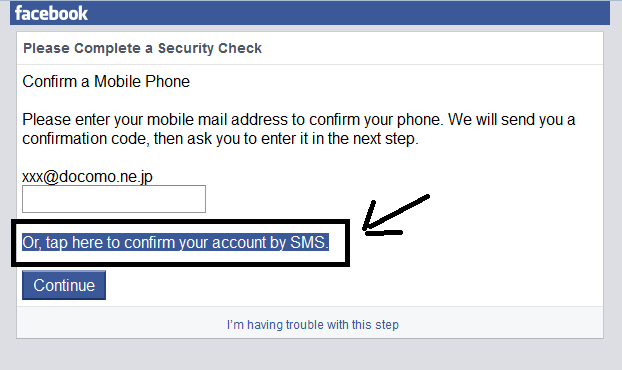
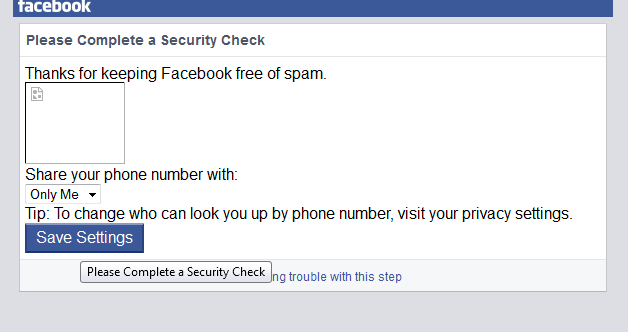
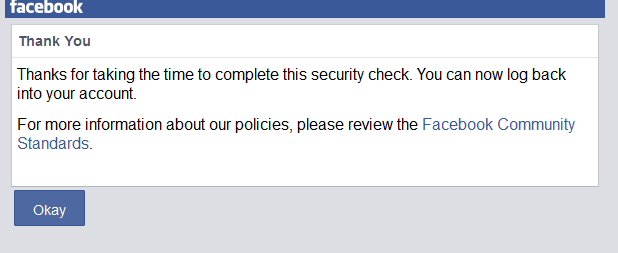
The first and very basic way of hacking Facebook accounts is via Phishing. Phishing is actually creating fake web pages to steal user’s credentials like email,passwords,phone no,etc.
DRAWBACK :
Users nowadays are aware of these type of attacks and one can not be easily fooled using this attack. You need some social engineering to trick someone.
‘
Prevention :
Always check the page URL before logging in. This is the most trusted and effective way one can use to avoid himself from phishing.
Other way is to use some good Antivirus software which will warn you if you visit a harmful phishing page.
Even if somehow you have already entered your credentials in a phisher, Immediately Change your password.
2) Keylogging :
This is another good way of hacking Facebook accounts. In this type of attack a hacker simply sends an infected file having keylogger in it to the victim. If the victim executes that file on his pc, whatever he types will be mailed/uploaded to hacker’s server. The advantage of this attack is that the victim won’t know that hacker is getting every Bit of data he is typing. Another big advantage is that hacker will get passwords of all the accounts used on that PC.
DRAWBACK :
Keyloggers are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
Execute the file only if you trust the sender.
Use online scanner such as novirusthanks.org
Use good antivirus and update it regularly .
3) Trojans/backdoors :
This is an advanced level topic. It consists of a server and a client. In this type of attack the attacker sends the infected server to the victim. After execution the infected server i.e. Trojan on the victim’s PC opens a backdoor and now the hacker can do whatever he wants with the victim’s PC .
DRAWBACK :
Trojans are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
Execute the file only if you trust the sender.
Use online scanner such as novirusthanks.org
Use good antivirus and update it regularly .
4)Sniffing
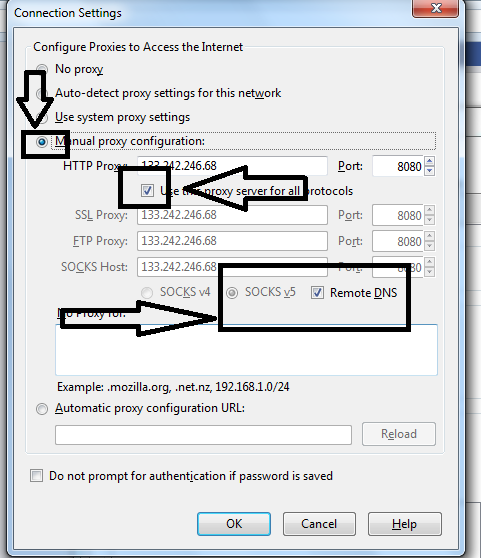
It consists of stealing session in progress. In this type of attack an attacker makes connection with server and client and relays message between them, making them believe that they are talking to each other directly.
DRAWBACK :
If user is logged out then attacker is also logged out and the session is lost.
It is difficult to sniff on SSL protected networks.
Prevention :
Always use SSL secured connections.
Always keep a look at the url if the http:// is not changed to https:// it means that sniffing is active on your network.
5)Social Engineering :
This method includes guessing and fooling the clients to give their own passwords. In this type of attack, a hacker sends a fake mail which is very convincing and appealing and asks the user for his password.
Answering the security questions also lies under this category.
Drawback :
It is not easy to convince someone to make him give his password.
Guessing generally doesn’t always work ( Although if you are lucky enough it may work!).
Prevention :
Never give your password to anyone
Don’t believe in any sort of emails which asks for your password
6) Session Hijacking
In a session hijacking attack an attacker steals victims cookies, cookies stores all the necessary logging Information about one’s account, using this info an attacker can easily hack anybody’s account. If you get the cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Facebook, Google, Yahoo.
Drawbacks :
You will be logged out when user is logged out.
You will not get the password of the user’s account.
Will not work if the user is using HTTPS connections.
Prevention :
Always work on SSL secured connections.
Always keep a look at the url if the http:// is not changed to https:// it means that sniffing is active on your network.
#cp
P.S. - Warning - The above content is just for learning purpose. Use these tricks at your own risk.
1) Phishing :
The first and very basic way of hacking Facebook accounts is via Phishing. Phishing is actually creating fake web pages to steal user’s credentials like email,passwords,phone no,etc.
DRAWBACK :
Users nowadays are aware of these type of attacks and one can not be easily fooled using this attack. You need some social engineering to trick someone.
‘
Prevention :
Always check the page URL before logging in. This is the most trusted and effective way one can use to avoid himself from phishing.
Other way is to use some good Antivirus software which will warn you if you visit a harmful phishing page.
Even if somehow you have already entered your credentials in a phisher, Immediately Change your password.
2) Keylogging :
This is another good way of hacking Facebook accounts. In this type of attack a hacker simply sends an infected file having keylogger in it to the victim. If the victim executes that file on his pc, whatever he types will be mailed/uploaded to hacker’s server. The advantage of this attack is that the victim won’t know that hacker is getting every Bit of data he is typing. Another big advantage is that hacker will get passwords of all the accounts used on that PC.
DRAWBACK :
Keyloggers are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
Execute the file only if you trust the sender.
Use online scanner such as novirusthanks.org
Use good antivirus and update it regularly .
3) Trojans/backdoors :
This is an advanced level topic. It consists of a server and a client. In this type of attack the attacker sends the infected server to the victim. After execution the infected server i.e. Trojan on the victim’s PC opens a backdoor and now the hacker can do whatever he wants with the victim’s PC .
DRAWBACK :
Trojans are often detected as threats by good antiviruses. Hacker must find a way to protect it from antivirus.
Prevention :
Execute the file only if you trust the sender.
Use online scanner such as novirusthanks.org
Use good antivirus and update it regularly .
4)Sniffing
It consists of stealing session in progress. In this type of attack an attacker makes connection with server and client and relays message between them, making them believe that they are talking to each other directly.
DRAWBACK :
If user is logged out then attacker is also logged out and the session is lost.
It is difficult to sniff on SSL protected networks.
Prevention :
Always use SSL secured connections.
Always keep a look at the url if the http:// is not changed to https:// it means that sniffing is active on your network.
5)Social Engineering :
This method includes guessing and fooling the clients to give their own passwords. In this type of attack, a hacker sends a fake mail which is very convincing and appealing and asks the user for his password.
Answering the security questions also lies under this category.
Drawback :
It is not easy to convince someone to make him give his password.
Guessing generally doesn’t always work ( Although if you are lucky enough it may work!).
Prevention :
Never give your password to anyone
Don’t believe in any sort of emails which asks for your password
6) Session Hijacking
In a session hijacking attack an attacker steals victims cookies, cookies stores all the necessary logging Information about one’s account, using this info an attacker can easily hack anybody’s account. If you get the cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Facebook, Google, Yahoo.
Drawbacks :
You will be logged out when user is logged out.
You will not get the password of the user’s account.
Will not work if the user is using HTTPS connections.
Prevention :
Always work on SSL secured connections.
Always keep a look at the url if the http:// is not changed to https:// it means that sniffing is active on your network.
#cp
P.S. - Warning - The above content is just for learning purpose. Use these tricks at your own risk.